Use a Password Manager to help
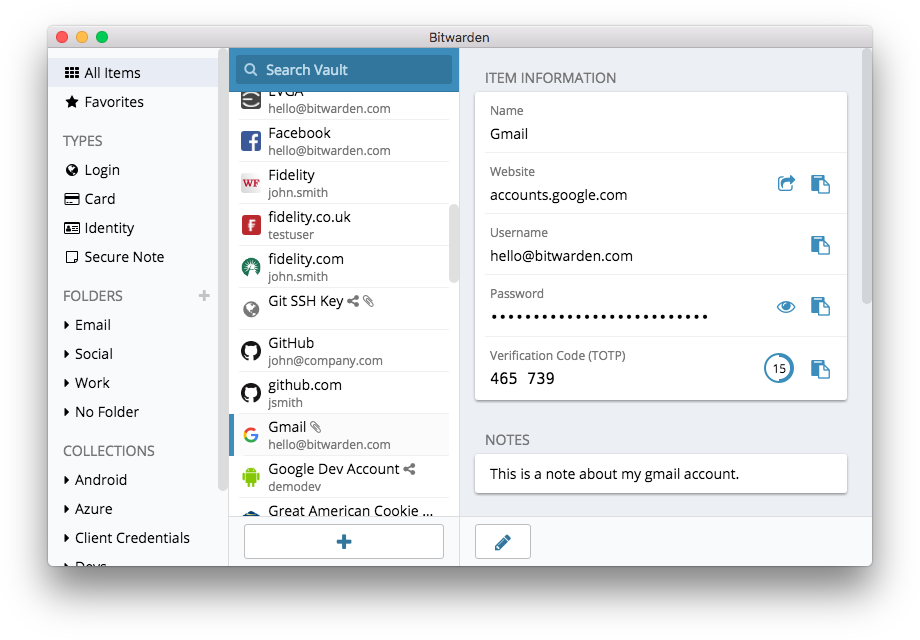
So you know it is important for everyone in the organization to use a long, random, and different password for each of their personal and organizational accounts, but how do you actually do that? Memorizing a good password for dozens (if not hundreds) of accounts is impossible, so everyone has to cheat. The wrong way to do it is to reuse passwords. Luckily, we can turn to digital password managers to make our lives much easier (and our password practices much safer) instead. These applications, many of which can be accessed via computer or mobile device, can create, store, and manage passwords for you and your entire organization. Adopting a secure password manager means that you will only ever have to remember one very strong, long password called the primary password (historically referred to as a “master” password), while being able to get the security benefits of using good, unique passwords across all of your accounts. You will use this primary password (and ideally a second factor of authentication (2FA), which will be discussed in the next section) to open your password manager and unlock access to all your other passwords. Password managers can also be shared across multiple accounts to facilitate secure password sharing throughout the organization.
Why do we need to use something new? Can we not just write them down on paper or in a spreadsheet on the computer?
Unfortunately, there are many common approaches to managing passwords that are not secure. Storing passwords on sheets of paper (unless you keep them locked away in a safe) can expose them to physical theft, prying eyes, and easy loss and damage. Saving passwords on a document on your computer makes it much easier for a hacker to gain access – or for someone who steals your computer to not only have your device but also access to all of your accounts. Using a good password manager is just as easy as that document, but far more secure.
Why should we trust a password manager?
Quality password managers go to extraordinary lengths (and employ excellent security teams) to keep their systems secure. Good password management apps (a few are recommended below) are also set up so that they do not have the ability to “unlock” your accounts. This means that in most cases, even if they were hacked or legally compelled to hand over information, they would not be able to lose or give up your passwords. It is also important to remember that it is infinitely more likely that an adversary guesses one of your weak or repeated passwords, or finds one in a public data breach, than that a good password manager would have its security systems broken. It is important to be skeptical, and you definitely should not blindly trust all software and applications, but reputable password managers have all the right incentives to do the right thing.
What about storing passwords in the browser?
Saving passwords in your browser is not the same as using a secure password manager. In short, you should not use Chrome, Firefox, Safari or any other browser as your password manager. Although it is definitely an improvement over writing them on paper or saving them in a spreadsheet, the basic password-saving features of your web browser leave something to be desired from a security perspective. These shortcomings also rob you of much of the convenience that a good password manager brings. Losing this convenience makes it more likely that people across your organization will continue poor password creation and sharing practices.
For example, unlike dedicated password managers, browsers’ built-in “save this password” or “remember this password” features do not provide simple mobile compatibility, cross-browser functionality, and strong password generation and auditing tools. These features are a big part of what makes a dedicated password manager so useful and beneficial to your organization’s security. Password managers also include organization-specific features (such as password sharing) that provide not just individual security value, but value to your organization as a whole.
If you have been saving passwords with your browser (intentionally or unintentionally), take a moment to remove them.